Saturday, October 15th 2011
Got A Virus? It's Your Fault Says Microsoft
Yes, that's right the maker of notoriously vulnerable software is now blaming you, the user, should you get a virus, trojan or other malware infection on your Windows computer. However, it does look like they have some justification for saying this. For those with long attention spans, Microsoft have just released their 168 page Microsoft Security Intelligence Report 6MB PDF, with the stated aim of providing:
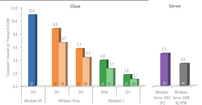
Next up are the well known operating system vulnerabilities. 32-bit XP SP3 is by far the most insecure of recent OS's, with 10.9 Computers Cleaned per Thousand (CCT) which is unsurprising, considering the many hundreds of patches required since its 2001 release. Vista SP1 32-bit is a bit better at 8.8 CCT (so much for the much-touted enhanced security at it's 2007 retail launch), with the 64-bit version somewhat better at 6.7 CCT. From there, OS security improves significantly with the best being Windows 7 SP1 64-bit, which is to be expected, at a low 1.1 CCT. Server infections are surprisingly high though, considering that they are based on the same code base as their client counterparts. For example, Server 2008 R2 has the same underlying code as Windows 7, yet it's CCT is 3.3 times higher, at 3.6. Why should this be, since the admins that run them can be assumed to know about patching and general good security practice?
Of infections due to third party software vulnerabilities, Java takes the cake with between one-third and one-half of all observed exploits. Again, old versions are the most vulnerable and as Java auto updates, there's really no excuse to be running such old versions.Because core OS security has increased so much in recent years, cybercriminals haven't stood still. Since duping uninformed "clueless" users is the most effective form of attack, they have now moved on to social networks in a big way, as they are so popular. Considering the type of fraudulent ads which can sometimes be seen on the side of a Facebook page, where the picture and text suggest one thing, but actually lead you to something completely different and obviously fraudulent when looked at a little more closely, it looks like the social networks themselves could do more to protect their users by vetting their advertisers more stringently.
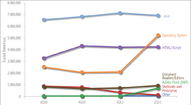
One significant enhancement to computer security, is Microsoft's proactive stance on eradicating botnets in the last few years. On several occasions now, stories have been published covering particular botnets that were taken down by Microsoft working together with law enforcement in various countries to track down the command and control servers and websites, putting them out of action and thus disrupting the botnet. The infected machines can then be cleaned up later. This writer has from personal experience, seen spam drop from up to around 50 items a day to maybe 6 or 7 per week which is a great improvement, so this strategy is clearly working.
The conclusion for such a big report is remarkably concise, so is quoted in full:
One thing that surprisingly wasn't mentioned in the report is the need to run a hardware edge firewall on your network. Without it, it's only a matter of time until Windows gets hacked into, regardless of how well patched it is. Thankfully, every decent modern home router has one of these built in and is switched on by default, addressing this critical requirement. For corporate networks, using a hardware firewall is a standard security policy decision.
Another worthy line of attack against botnets is the ISP. In some cases, ISP's monitor their user's internet connections, looking for patterns of behaviour that indicates a compromised machine. If found, they notify the user, usually by email. They may also slow down the connection, filter it or turn off access completely, depending on the user agreeemnt and the severity of the attacks, until the customer has addressed the problem
Due to its 168 pages, the report is very detailed and covers a wide range of topics, so covering them all is beyond the scope of this story. However, some of the more interesting areas covered in the report are: the rising attacks on Android smartphones, Flash Player exploits, spam, phishing and malware sites, rogue security software, Process Explorer and strategies for eradication of malware from infected machines.
Finally, the big takeaway from this report, is the usual advice of running the latest versions of all your software, including the OS (64-bit where possible) patch it as patches are released, use internet security software, use a hardware firewall and of course not forgetting user savvy to avoid getting duped by social engineering tricks into doing something stupid. Reckless user behaviour is by far the biggest part of this problem, just like car accidents.
Sources:
InfoWorld, Microsoft Security Intelligence Report 2011
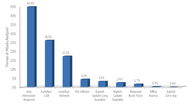
An in-depth perspective on software vulnerabilities and exploits, malicious code threats, and potentially unwanted software in the first half of 2011The first thing to note about the report is that it is limited to its Malicious Software Removal Tool and Microsoft's other anti-malware products. Zero-day attacks that it can't detect are not included in the findings. So, surely it can't all be the user's fault then? It also means that the security angles from third party security vendors such as Kaspersky, Norton and McAfee aren't represented here.By far the biggest attack vector with 44.8% is infection with the help of the user, where they're duped into running some dodgy attachment or clicking an equally dodgy link. What with the generally very low level of computer literacy of most ordinary users, this is hardly surprising. Taking second and third place are two autorun options, USB at 26% & network at 17.2%, with all the others at surprisingly low levels, especially the exploit when update is long available, standing at only 3.2%.
Next up are the well known operating system vulnerabilities. 32-bit XP SP3 is by far the most insecure of recent OS's, with 10.9 Computers Cleaned per Thousand (CCT) which is unsurprising, considering the many hundreds of patches required since its 2001 release. Vista SP1 32-bit is a bit better at 8.8 CCT (so much for the much-touted enhanced security at it's 2007 retail launch), with the 64-bit version somewhat better at 6.7 CCT. From there, OS security improves significantly with the best being Windows 7 SP1 64-bit, which is to be expected, at a low 1.1 CCT. Server infections are surprisingly high though, considering that they are based on the same code base as their client counterparts. For example, Server 2008 R2 has the same underlying code as Windows 7, yet it's CCT is 3.3 times higher, at 3.6. Why should this be, since the admins that run them can be assumed to know about patching and general good security practice?
Of infections due to third party software vulnerabilities, Java takes the cake with between one-third and one-half of all observed exploits. Again, old versions are the most vulnerable and as Java auto updates, there's really no excuse to be running such old versions.Because core OS security has increased so much in recent years, cybercriminals haven't stood still. Since duping uninformed "clueless" users is the most effective form of attack, they have now moved on to social networks in a big way, as they are so popular. Considering the type of fraudulent ads which can sometimes be seen on the side of a Facebook page, where the picture and text suggest one thing, but actually lead you to something completely different and obviously fraudulent when looked at a little more closely, it looks like the social networks themselves could do more to protect their users by vetting their advertisers more stringently.
One significant enhancement to computer security, is Microsoft's proactive stance on eradicating botnets in the last few years. On several occasions now, stories have been published covering particular botnets that were taken down by Microsoft working together with law enforcement in various countries to track down the command and control servers and websites, putting them out of action and thus disrupting the botnet. The infected machines can then be cleaned up later. This writer has from personal experience, seen spam drop from up to around 50 items a day to maybe 6 or 7 per week which is a great improvement, so this strategy is clearly working.
The conclusion for such a big report is remarkably concise, so is quoted in full:
Unfortunately, the process of eliminating malware from a computer is likely to become much harder in the next few years. Malware has become a lucrative business for the criminals who create and distribute it, and they have a financial incentive to find new ways to evade detection and make malicious files and processes harder to remove.Overall though, it doesn't seem like infections are down much, with social media phishing taking up the slack as clueless users blindly run malware and click on bad links. It would be desirable if the overall rate dropped, so that criminals would be put out of business and be forced to work for a living like everyone else or preferably, sit in jail.
Therefore, understanding how malware spreads, operates, and defends itself at a fundamental level should be considered a prerequisite for IT professionals charged with protecting their users from attack and containing outbreaks when they occur. However, the best guidance is that which helps prevent malware infection from ever occurring. For more information about how to prevent malware infection, see the Microsoft Malware Protection Center at www.microsoft.com/security/portal.
One thing that surprisingly wasn't mentioned in the report is the need to run a hardware edge firewall on your network. Without it, it's only a matter of time until Windows gets hacked into, regardless of how well patched it is. Thankfully, every decent modern home router has one of these built in and is switched on by default, addressing this critical requirement. For corporate networks, using a hardware firewall is a standard security policy decision.
Another worthy line of attack against botnets is the ISP. In some cases, ISP's monitor their user's internet connections, looking for patterns of behaviour that indicates a compromised machine. If found, they notify the user, usually by email. They may also slow down the connection, filter it or turn off access completely, depending on the user agreeemnt and the severity of the attacks, until the customer has addressed the problem
Due to its 168 pages, the report is very detailed and covers a wide range of topics, so covering them all is beyond the scope of this story. However, some of the more interesting areas covered in the report are: the rising attacks on Android smartphones, Flash Player exploits, spam, phishing and malware sites, rogue security software, Process Explorer and strategies for eradication of malware from infected machines.
Finally, the big takeaway from this report, is the usual advice of running the latest versions of all your software, including the OS (64-bit where possible) patch it as patches are released, use internet security software, use a hardware firewall and of course not forgetting user savvy to avoid getting duped by social engineering tricks into doing something stupid. Reckless user behaviour is by far the biggest part of this problem, just like car accidents.
105 Comments on Got A Virus? It's Your Fault Says Microsoft
I haven't used windows firewall since xp (off and uninstalled) since it would restrict my bandwidth when I used emule. Nowadays I just run aviara, malwarebytes, spybot every now and then. Haven't had a problem in yrs. I had only one virus that would reset my pc during post/window logon. Only fix was being fast enough to get into bios and enter safe mode to format. Been clean ever since.
Isn't there something like an ip tracker or something that you can use to block and trace (to shut them down) those annoying spam emails? A lot of people get those stupid lottery or a relative past away in some weird country and left you their whole estate. I would love to stop all that annoying spam. I tried replying back a few times telling them to stop but it just comes back as undeliverable.
That's like saying all Ford cars are now unsafe because Pintos exploded into fireballs in wrecks in the 70's.
you cant fix stupid...
Why couldn't the OS come with whatever it was the patch fixed to begin with? If so, Blaster wouldn't exist since there was no whatever-it-was to be exploited.Much more secure, sure: with this i can agree.
Still, and to use an analogy:
I see loads of topics where people mention the hate of Seagate HDDs because this or that happened in the past. Why don't you explain to them "That was in the past: it's much safer now!" and see what their reaction is.
It's ballsy to claim most viruses are user fault when you're the maker of the software which allows for so much hacks: poorly coded? Dunno, really.
No matter how many times you tell people about safe browsing practices, there are always those who come back saying "I didn't install that!" or have some spoof AV software telling them that their hard drive is mechanically damaged by a virus and it can be fixed by buying some software :rolleyes:
Nobody has ever complained about free antivirus software, or about having less ads on their webpages. ABP blocks 90% of what users click on and get infected, and it increases the chances of the person using FF instead of dropping right back into using IE6.0 with 80000 toolbars
Why don't they create a team who's only job is to try and hack their OS? If they find the coding problems before the product is shipped to customers, it would help them, no?
Think of it as prevention rather then reaction: why wait for hackers and what not to find exploits and risk major problems if you can pay someone to do it and fix the problem before it reaches the end user?
I more secure system also means more restrictions.
Hackers gonna hack - thats correct. but depending how good they are, they are most likely only possible to use that virus or exploit a number of times before it gets patched over.
i don't have had a virus in like 2 years
But like the old joke about 2 guys running from a bear, the average hacker doesn't have to be better than every other hacker, he just has to be better than the average user - and that ain't askin' a whole lot.
The average user assumes everything is secure, which is the worst kind of security.
Personally. Ive had win 7 installed on my new pc over a month, with no extra security other than what windows offers, and have had 0 infections. But hey how would i know i have no a/v to check!
As for malware, every person whose computer I have to work on regularly has one thing in common. They all use Internet Explorer. Those who use FF or Opera don't seem to get as many problems. Can you run IE safely? Certainly, but with default settings, the average user's PC will be full of crap in a few hours of running IE.
from email, attachment, removable things
so it aint a surprise if said like that, and one more no matter what the largest os will be a good target to attack