- Joined
- Feb 14, 2012
- Messages
- 2,388 (0.49/day)
| System Name | msdos |
|---|---|
| Processor | 8086 |
| Motherboard | mainboard |
| Cooling | passive |
| Memory | 640KB + 384KB extended |
| Video Card(s) | EGA |
| Storage | 5.25" |
| Display(s) | 80x25 |
| Case | plastic |
| Audio Device(s) | modchip |
| Power Supply | 45 watts |
| Mouse | serial |
| Keyboard | yes |
| Software | disk commander |
| Benchmark Scores | still running |
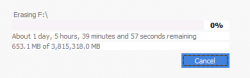
Just boot any linux, and "dd if=/dev/zero of=/dev/sd[...] bs=1M" if you need to super secure wipe [multiple pass with random data] because someone is going to disassemble the drive and analyze residual write strength, you probably have other problems already ...