D
Deleted member 185158
Guest
Ill never see the warning haha.
Your estimation of the average user needs adjustment. The general public is getting much better at proper PC security and the one that aren't are wise enough to ask for help in doing so.The average user doesn't lock down their system
That is a rarity, an exception rather that the rule because...this why a corporate network will kill a port you plug an xp or Vista computer into.
only if said network is improperly and/or poorly secured.And yes one machine can compromise a network.
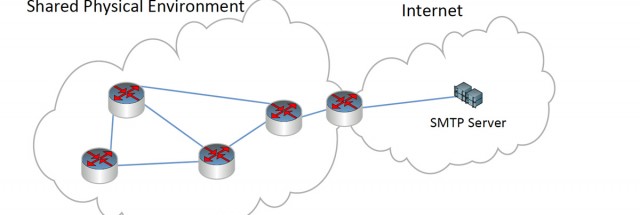
That depends greatly on how file-sharing is used, how it's provisioned and what permissions are configured.Let's say that you have file sharing turned on
Thanks for the advice. However, I've been working on and securing PC's, LAN's, WAN's and the such for nearly 30 years and am very good at it. I think I'm going to continue to rely on my experience where it comes to how, when and why to secure a system and a network. Thank You.Do a course on information security it's spelled out clearly.
| System Name | The86 |
|---|---|
| Processor | Ryzen 5 3600 |
| Motherboard | ASROCKS B450 Steel Legend |
| Cooling | AMD Stealth |
| Memory | 2x8gb DDR4 3200 Corsair |
| Video Card(s) | EVGA RTX 3060 Ti |
| Storage | WD Black 512gb, WD Blue 1TB |
| Display(s) | AOC 24in |
| Case | Raidmax Alpha Prime |
| Power Supply | 700W Thermaltake Smart |
| Mouse | Logitech Mx510 |
| Keyboard | Razer BlackWidow 2012 |
| Software | Windows 10 Professional |
Your estimation of the average user needs adjustment. The general public is getting much better at proper PC security and the one that aren't are wise enough to ask for help in doing so.
That is a rarity, an exception rather that the rule because...
only if said network is improperly and/or poorly secured.
That depends greatly on how file-sharing is used, how it's provisioned and what permissions are configured.
Thanks for the advice. However, I've been working on and securing PC's, LAN's, WAN's and the such for nearly 30 years and am very good at it. I think I'm going to continue to rely on my experience where it comes to how, when and why to secure a system and a network. Thank You.
| System Name | Pioneer |
|---|---|
| Processor | Ryzen R9 7950X |
| Motherboard | GIGABYTE Aorus Elite X670 AX |
| Cooling | Noctua NH-D15 + A whole lotta Sunon and Corsair Maglev blower fans... |
| Memory | 64GB (4x 16GB) G.Skill Flare X5 @ DDR5-6000 CL30 |
| Video Card(s) | XFX RX 7900 XTX Speedster Merc 310 |
| Storage | 2x Crucial P5 Plus 2TB PCIe 4.0 NVMe SSDs |
| Display(s) | 55" LG 55" B9 OLED 4K Display |
| Case | Thermaltake Core X31 |
| Audio Device(s) | TOSLINK->Schiit Modi MB->Asgard 2 DAC Amp->AKG Pro K712 Headphones or HDMI->B9 OLED |
| Power Supply | FSP Hydro Ti Pro 850W |
| Mouse | Logitech G305 Lightspeed Wireless |
| Keyboard | WASD Code v3 with Cherry Green keyswitches + PBT DS keycaps |
| Software | Gentoo Linux x64 |
For those of us who manually control our services, we will not see such prompts.
Not difficult really. I selectively do manual installs of updates.As long as you do not install the update and/or track down the service and/or scheduled task it installs, sure.
| System Name | Pioneer |
|---|---|
| Processor | Ryzen R9 7950X |
| Motherboard | GIGABYTE Aorus Elite X670 AX |
| Cooling | Noctua NH-D15 + A whole lotta Sunon and Corsair Maglev blower fans... |
| Memory | 64GB (4x 16GB) G.Skill Flare X5 @ DDR5-6000 CL30 |
| Video Card(s) | XFX RX 7900 XTX Speedster Merc 310 |
| Storage | 2x Crucial P5 Plus 2TB PCIe 4.0 NVMe SSDs |
| Display(s) | 55" LG 55" B9 OLED 4K Display |
| Case | Thermaltake Core X31 |
| Audio Device(s) | TOSLINK->Schiit Modi MB->Asgard 2 DAC Amp->AKG Pro K712 Headphones or HDMI->B9 OLED |
| Power Supply | FSP Hydro Ti Pro 850W |
| Mouse | Logitech G305 Lightspeed Wireless |
| Keyboard | WASD Code v3 with Cherry Green keyswitches + PBT DS keycaps |
| Software | Gentoo Linux x64 |
Your welcome to follow your flawed knowledge, it's the guys stuck in their ways that have caused the biggest problems for companies, and yes every company I've worked for will kill a port if you plug in a system that has an outdated OS that gets no support, and will refuse guest wifi for the same reason, it's seen as smart and removes risks. Also the average user is the same as they have always been, can they use it better yes, but they still can't wrap their head around security, there is a reason information security is the fastest growing sector in IT, it's because the average person is clueless. I'm just glad your not incharge of info sec where i work, I'd hate to keep cleaning up the mess such policies would cause.
Not difficult really. I selectively do manual installs of updates.
Thank You, and you.Your welcome to follow your flawed knowledge
Incorrect, it is the ignorant or incompetent network admins who fail to properly configure networks that allow for network problems.it's the guys stuck in their ways that have caused the biggest problems for companies
I regularly travel and have only seen this kind of thing on poorly configured networks.and yes every company I've worked for will kill a port if you plug in a system that has an outdated OS that gets no support
Again, that estimation of the average user needs adjustment.Also the average user is the same as they have always been, can they use it better yes, but they still can't wrap their head around security, there is a reason information security is the fastest growing sector in IT, it's because the average person is clueless.
Just an FYI, if I were working at your company, it would likely be as the director of IT services and you would get proper training in short order.I'm just glad your not incharge of info sec where i work, I'd hate to keep cleaning up the mess such policies would cause.
Exactly right.Me too. God, WSUS has saved us from so much W10 rollout pain.
| Processor | i7 8700k 4.6Ghz @ 1.24V |
|---|---|
| Motherboard | AsRock Fatal1ty K6 Z370 |
| Cooling | beQuiet! Dark Rock Pro 3 |
| Memory | 16GB Corsair Vengeance LPX 3200/C16 |
| Video Card(s) | ASRock RX7900XT Phantom Gaming |
| Storage | Samsung 850 EVO 1TB + Samsung 830 256GB + Crucial BX100 250GB + Toshiba 1TB HDD |
| Display(s) | Gigabyte G34QWC (3440x1440) |
| Case | Fractal Design Define R5 |
| Audio Device(s) | Harman Kardon AVR137 + 2.1 |
| Power Supply | EVGA Supernova G2 750W |
| Mouse | XTRFY M42 |
| Keyboard | Lenovo Thinkpad Trackpoint II |
| Software | W10 x64 |
Does that mean I should think about updating my WinXP machines?


Making a system immune is, admittedly, a much more involved process. However once implemented, the system in question is far easier to maintain. When you apply such methods to an entire network, keeping things in order is much less troublesome.It's two different mindsets, prevention and immunity. One is much harder to maintain and really easy to screw up, especially with zero days. But if you really can pull off immunity, it's honestly better.
Very true. Most security suites that still support it are doing so more effectively as of late. Third party software firewalls are also proving to still be very effective.XP might actually get safer again because the market share is so low, nobody cares.
| System Name | Brightworks Systems BWS-6 E-IV |
|---|---|
| Processor | Intel Core i5-6600 @ 3.9GHz |
| Motherboard | Gigabyte GA-Z170-HD3 Rev 1.0 |
| Cooling | Quality case, 2 x Fractal Design 140mm fans, stock CPU HSF |
| Memory | 32GB (4 x 8GB) DDR4 3000 Corsair Vengeance |
| Video Card(s) | EVGA GEForce GTX 1050Ti 4Gb GDDR5 |
| Storage | Samsung 850 Pro 256GB SSD, Samsung 860 Evo 500GB SSD |
| Display(s) | Samsung S24E650BW LED x 2 |
| Case | Fractal Design Define R4 |
| Power Supply | EVGA Supernova 550W G2 Gold |
| Mouse | Logitech M190 |
| Keyboard | Microsoft Wireless Comfort 5050 |
| Software | W10 Pro 64-bit |
I agree that no one is encouraging people to compromise security. But more should be done to encourage folks to let W7 go and move to the more secure operating system. It is not like Microsoft has not given us enough time.No one is doing that. Just because Microsoft has ended support doesn't mean everyone else making security suites will. As mentioned elsewhere, many have stated they will continue support on 7 for the next few years. Additionally, 7 isn't going to fall apart.
It is not really a flawed conclusion but it is being sensationalized and blown out of proportion with fear-mongering and exaggerated claims. I agree with that you 100% that a compromised W7 computer does mean my computer will soon be compromised. It won't. But a compromised W7 computer (just like a compromised XP computer) can and likely will be used to attack me, our banks and our institutions. Those compromised systems are likely to be used to distribute spam, malware (including ransomware), or used as zombies in bot armies conducting DDoS attacks on our government networks, power grids, banks, hospitals, facebook and others. With some of those attacks backed by Russia, China, N. Korea, Iran and other very malicious state sponsored players.Rubbish. That is a flawed conclusion based on fear-mongering and little else. One compromised system does not automatically compromise every other system. System vulnerabilities are based as much on secure computing methodologies as it does well structured code.

Now this is flawed. You assume because it is easy for you to keep your system secure by selectively installing updates, that it is easy for anyone to do that. That's just wrong. Some folks are totally clueless when it comes this stuff, others could care less. And that's fine. NO ONE should need to be a security expert to keep their Windows computer secured.Not difficult really. I selectively do manual installs of updates.
This is true. What I suppose many people think is that Microsoft has not given us a worthy alternative. This is the gist of why people are hesitant to move forward, myself included.It is not like Microsoft has not given us enough time.
No one is saying that, per se. All I'm trying to convey is that with proper effort 7 and even XP before it are securable.Anyone who claims W7 is inherently more secure than W10 is ignoring the facts and sticking their heads in the sand.
Exactly. There is a lot of money to be made in providing what Microsoft won't and as long as the money can be made, support will continue and will be effective.I also agree with Lex that security program developers are not going to suddenly stop supporting W7
True. However history has shown that all but handful can be mitigated, and isolation efforts are very effective against those remaining few.It is not a given that all future vulnerabilities can be protected. And that's the problem - the unknown.
There is a difference between being stubborn and standing one's ground. Please know that the moment Windows 7 can not be properly secured, I will stop allowing it on the net. My lone XP system is only allowed on the net for short periods and then only for specific purposes. When it does, it's behind a properly configured software firewall and hardware firewall. Windows 7 will face that same fate, but that time has not come.We must view the decline in W7's security as inevitable. Stop being so stubborn and move to W10, or Linux.
| System Name | Brightworks Systems BWS-6 E-IV |
|---|---|
| Processor | Intel Core i5-6600 @ 3.9GHz |
| Motherboard | Gigabyte GA-Z170-HD3 Rev 1.0 |
| Cooling | Quality case, 2 x Fractal Design 140mm fans, stock CPU HSF |
| Memory | 32GB (4 x 8GB) DDR4 3000 Corsair Vengeance |
| Video Card(s) | EVGA GEForce GTX 1050Ti 4Gb GDDR5 |
| Storage | Samsung 850 Pro 256GB SSD, Samsung 860 Evo 500GB SSD |
| Display(s) | Samsung S24E650BW LED x 2 |
| Case | Fractal Design Define R4 |
| Power Supply | EVGA Supernova 550W G2 Gold |
| Mouse | Logitech M190 |
| Keyboard | Microsoft Wireless Comfort 5050 |
| Software | W10 Pro 64-bit |
I think there are better battles to choose to fight (like the ridiculous prices for smart phones or even MS Office). W10 is a worthy alternative and really not that expensive. All folks need to do to realize that is to give W10 a fair shake. They need to take the time to get past their biases and the small learning curve and get used to it.What I suppose many people think is that Microsoft has not given us a worthy alternative.
There is a difference between being stubborn and standing one's ground.
| System Name | The86 |
|---|---|
| Processor | Ryzen 5 3600 |
| Motherboard | ASROCKS B450 Steel Legend |
| Cooling | AMD Stealth |
| Memory | 2x8gb DDR4 3200 Corsair |
| Video Card(s) | EVGA RTX 3060 Ti |
| Storage | WD Black 512gb, WD Blue 1TB |
| Display(s) | AOC 24in |
| Case | Raidmax Alpha Prime |
| Power Supply | 700W Thermaltake Smart |
| Mouse | Logitech Mx510 |
| Keyboard | Razer BlackWidow 2012 |
| Software | Windows 10 Professional |
Just an FYI, if I were working at your company, it would likely be as the director of IT services and you would get proper training in short order.
It's two different mindsets, prevention and immunity. One is much harder to maintain and really easy to screw up, especially with zero days. But if you really can pull off immunity, it's honestly better.
In a high security environment, I preach both. Most cases can do with one though.
Me too. God, WSUS has saved us from so much W10 rollout pain.
| System Name | Brightworks Systems BWS-6 E-IV |
|---|---|
| Processor | Intel Core i5-6600 @ 3.9GHz |
| Motherboard | Gigabyte GA-Z170-HD3 Rev 1.0 |
| Cooling | Quality case, 2 x Fractal Design 140mm fans, stock CPU HSF |
| Memory | 32GB (4 x 8GB) DDR4 3000 Corsair Vengeance |
| Video Card(s) | EVGA GEForce GTX 1050Ti 4Gb GDDR5 |
| Storage | Samsung 850 Pro 256GB SSD, Samsung 860 Evo 500GB SSD |
| Display(s) | Samsung S24E650BW LED x 2 |
| Case | Fractal Design Define R4 |
| Power Supply | EVGA Supernova 550W G2 Gold |
| Mouse | Logitech M190 |
| Keyboard | Microsoft Wireless Comfort 5050 |
| Software | W10 Pro 64-bit |
| System Name | The86 |
|---|---|
| Processor | Ryzen 5 3600 |
| Motherboard | ASROCKS B450 Steel Legend |
| Cooling | AMD Stealth |
| Memory | 2x8gb DDR4 3200 Corsair |
| Video Card(s) | EVGA RTX 3060 Ti |
| Storage | WD Black 512gb, WD Blue 1TB |
| Display(s) | AOC 24in |
| Case | Raidmax Alpha Prime |
| Power Supply | 700W Thermaltake Smart |
| Mouse | Logitech Mx510 |
| Keyboard | Razer BlackWidow 2012 |
| Software | Windows 10 Professional |
While I think candle_86's comments may be a bit harsh, in general, I agree with them. Businesses had lots of advanced notice this was coming. But as a business owner, even as a very small business owner, spending money on IS/IT hardware, software, training and support can be real challenging because for most businesses, none of that "makes" any money for the business. Its like paying the rent or the electric bill or buying desks and chairs and tables. Its all part of "overhead" and comes right off the top before any profits. It can be tough.
So I'm not buying "zero excuse" for all. But certainly for most. And for sure, with home users, IMO, that gets even closer to zero. Why? Because NOBODY "needs" a fancy "gaming" rig. If they "need" a computer for work or school or pay bills, Linux and LibreOffice work fine. New W10 computers can be had for less than $400. Refurbished for less than that.
That is what is at the heart of this debate. Whether Windows 10 is a worthy replacement. Many disagree with you and the reasoning for such is legitimately worrisome. The expense is not one of those reasons.W10 is a worthy alternative and really not that expensive.
You say that like you think no one has. I have been trying to give 10 a "fair shake" since it's release. It is still only barely workable by the standards I require for my personal systems. Making it workable is like pulling teeth from a cranky rhino, it can be done, but it's a hassle.All folks need to do to realize that is to give W10 a fair shake.
The learning curve isn't the problem. It's the plethora of small but serious limitations imposed by Microsoft on how the system can and can not be configured, how it's GUI can and can not be configured and/or customized.They need to take the time to get past their biases and the small learning curve and get used to it.
No, it can't without serious hacks to the system files, which certain people will whine about the security of..It is easy to configure to make it look and feel like W7.
Telling someone that they're an "idiot" for not upgrading is not productive. Had you said that to me, you would have been escorted off the property by security and would be brushing up on your resume. You would not get a reference. And yes, I've had to do that.Considering I'm certified I'd call any IT Director that directed us to turn off updates long term and stay on Windows 7 an idiot, matter of fact i did that to a boss once that suggested we stick on XP for a while past the end of support.
| System Name | Brightworks Systems BWS-6 E-IV |
|---|---|
| Processor | Intel Core i5-6600 @ 3.9GHz |
| Motherboard | Gigabyte GA-Z170-HD3 Rev 1.0 |
| Cooling | Quality case, 2 x Fractal Design 140mm fans, stock CPU HSF |
| Memory | 32GB (4 x 8GB) DDR4 3000 Corsair Vengeance |
| Video Card(s) | EVGA GEForce GTX 1050Ti 4Gb GDDR5 |
| Storage | Samsung 850 Pro 256GB SSD, Samsung 860 Evo 500GB SSD |
| Display(s) | Samsung S24E650BW LED x 2 |
| Case | Fractal Design Define R4 |
| Power Supply | EVGA Supernova 550W G2 Gold |
| Mouse | Logitech M190 |
| Keyboard | Microsoft Wireless Comfort 5050 |
| Software | W10 Pro 64-bit |
| System Name | The86 |
|---|---|
| Processor | Ryzen 5 3600 |
| Motherboard | ASROCKS B450 Steel Legend |
| Cooling | AMD Stealth |
| Memory | 2x8gb DDR4 3200 Corsair |
| Video Card(s) | EVGA RTX 3060 Ti |
| Storage | WD Black 512gb, WD Blue 1TB |
| Display(s) | AOC 24in |
| Case | Raidmax Alpha Prime |
| Power Supply | 700W Thermaltake Smart |
| Mouse | Logitech Mx510 |
| Keyboard | Razer BlackWidow 2012 |
| Software | Windows 10 Professional |
Telling someone that they're an "idiot" for not upgrading is not productive. Had you said that to me, you would have been escorted off the property by security and would be brushing up on your resume. You would not get a reference. And yes, I've had to do that.
Let's just agree to disagree and call it good. Happy New Year!There is no excuse for not following industry best practices period.
| System Name | Pioneer |
|---|---|
| Processor | Ryzen R9 7950X |
| Motherboard | GIGABYTE Aorus Elite X670 AX |
| Cooling | Noctua NH-D15 + A whole lotta Sunon and Corsair Maglev blower fans... |
| Memory | 64GB (4x 16GB) G.Skill Flare X5 @ DDR5-6000 CL30 |
| Video Card(s) | XFX RX 7900 XTX Speedster Merc 310 |
| Storage | 2x Crucial P5 Plus 2TB PCIe 4.0 NVMe SSDs |
| Display(s) | 55" LG 55" B9 OLED 4K Display |
| Case | Thermaltake Core X31 |
| Audio Device(s) | TOSLINK->Schiit Modi MB->Asgard 2 DAC Amp->AKG Pro K712 Headphones or HDMI->B9 OLED |
| Power Supply | FSP Hydro Ti Pro 850W |
| Mouse | Logitech G305 Lightspeed Wireless |
| Keyboard | WASD Code v3 with Cherry Green keyswitches + PBT DS keycaps |
| Software | Gentoo Linux x64 |
Immunity is impossible unless you airgap your network, otherwise there is also a hole, maybe it hasn't been discovered yet. This is something they teach in any class and part of any info sec certification test, there is no effective way to have a system connected to the internet and have it immune, it's impossible.
| Processor | Ryzen 2700X |
|---|---|
| Motherboard | X470 Tachi Ultimate |
| Cooling | Scythe Big Shuriken 3 |
| Memory | C.R.S. |
| Video Card(s) | Radeon VII |
| Software | Win 7 |
| Benchmark Scores | Never high enough |
Same here.Ill never see the warning haha.

How so?I would also note even airgaps aren't entirely secure.
| System Name | The86 |
|---|---|
| Processor | Ryzen 5 3600 |
| Motherboard | ASROCKS B450 Steel Legend |
| Cooling | AMD Stealth |
| Memory | 2x8gb DDR4 3200 Corsair |
| Video Card(s) | EVGA RTX 3060 Ti |
| Storage | WD Black 512gb, WD Blue 1TB |
| Display(s) | AOC 24in |
| Case | Raidmax Alpha Prime |
| Power Supply | 700W Thermaltake Smart |
| Mouse | Logitech Mx510 |
| Keyboard | Razer BlackWidow 2012 |
| Software | Windows 10 Professional |
I was speaking conceptually, not globally.
Of course that's true. It's sort of "no duh" at this point.
I would also note even airgaps aren't entirely secure.
| System Name | BorgX79 |
|---|---|
| Processor | i7-3930k 6/12cores@4.4GHz |
| Motherboard | Sabertoothx79 |
| Cooling | Capitan 360 |
| Memory | Muhskin DDR3-1866 |
| Video Card(s) | Sapphire R480 8GB |
| Storage | Chronos SSD |
| Display(s) | 3x VW266H |
| Case | Ching Mien 600 |
| Audio Device(s) | Realtek |
| Power Supply | Cooler Master 1000W Silent Pro |
| Mouse | Logitech G900 |
| Keyboard | Rosewill RK-1000 |
| Software | Win7x64 |
| Processor | Ryzen 9 5900X |
|---|---|
| Motherboard | MSI B450 Tomahawk ATX |
| Cooling | Cooler Master Hyper 212 Black Edition |
| Memory | VENGEANCE LPX 2 x 16GB DDR4-3600 C18 OCed 3800 |
| Video Card(s) | XFX Speedster SWFT309 AMD Radeon RX 6700 XT CORE Gaming |
| Storage | 970 EVO NVMe M.2 500 GB, 870 QVO 1 TB |
| Display(s) | Samsung 28” 4K monitor |
| Case | Phantek Eclipse P400S (PH-EC416PS) |
| Audio Device(s) | EVGA NU Audio |
| Power Supply | EVGA 850 BQ |
| Mouse | SteelSeries Rival 310 |
| Keyboard | Logitech G G413 Silver |
| Software | Windows 10 Professional 64-bit v22H2 |
piezoelectric speakers.How so?