- Joined
- Apr 11, 2021
- Messages
- 837 (0.56/day)
- Location
- ÐҼƱ₸ꞨƇҤՆԹՌÐ
| System Name | °( ఠ ͟ʖ ఠ)° |
|---|---|
| Processor | Intel | i7 _ 11700K | @ ~ 5GHz all | cooling ~ Thermal Grizzly CARBONAUT |
| Motherboard | Asus | ROG Strix -- Z 590-E wifi |
| Cooling | Asus | ROG Ryujin 240 2* _Noctua F PPC °3000 | 4+1* _beQuiet_ Silent/Light Wings 3 °2200 |
| Memory | G Skill | Trident Z *RGB @ 4000_ | _15-15-15-36_ | |
| Video Card(s) | Asus | ROG Strix -- RTX 3070Ti_ #OC Edition |
| Storage | WD black | Samsung EVO 860 / 970 EVO plus| WDC WD40 | Intenso x2 |
| Display(s) | Alienware | AW3821DW _ 38" {3840*1600} wide - curved |
| Case | be Quiet | DARK BASE PRO 900 --- _rev. 2 --- #Silver |
| Audio Device(s) | Asus | ROG Throne - Qi_7.1 | LOGITECH_G560 Speaker (RGB) |
| Power Supply | be Quiet | DARK Power PRO 12 __ 1200W *titanium |
| Mouse | Razer | NAGA Trinity (19 buttons) |
| Keyboard | Razer | Huntsman V2 analog | Razer Goliathus (RGB) black |
| VR HMD | Razer | Kraken Ultimate HEADSET __7.1 THX ____| DX RACER - Gaming Leather Chair_____ VR?? is odd! |
| Software | Windows ɧ.eliX |
| Benchmark Scores | See signature URL |
Greetings,
after an exciting week of trial and error and finding out which unknown person spoofed under my running operating system, reprogrammed my hard drive header and installed a virtual drive to infect my windows so that you don't notice it.
it was found:
3MB virtual boot lead to
8MB boot in MBR format may lead to
17MB and 230MB GPT boot+efi which lead to
1,8GB OS in form of about size revi.os and to a total of
2,8GB of unused harddisk space.
i was able to extract a registration file from this virtual OS (win) and save it in *.TXT format. i also disabled it as a precaution.
does anyone have a hot wire or expertise, an idea or good tricks?
at this point i am currently stuck except that i have been able to isolate everything so far to prevent and no longer allow this connection from my own computer to the other.
i put the file on my google drive since it is quite large (115MB) and cannot be uploaded here.
THE FILE IS A
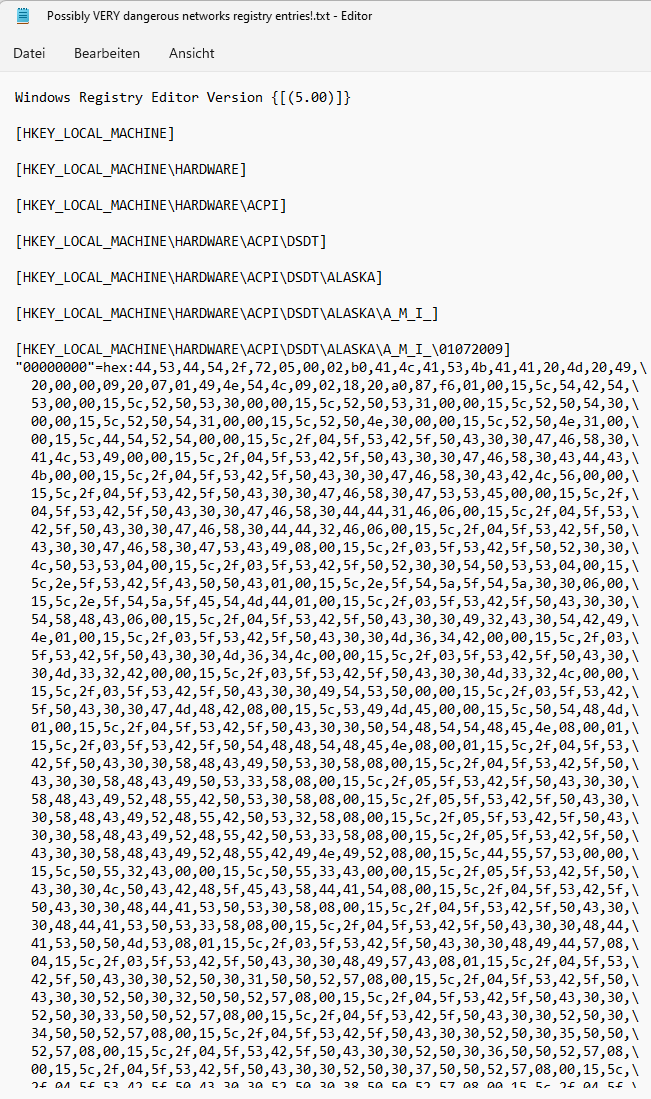
*:TXT
contains all information about this #network under my windows version
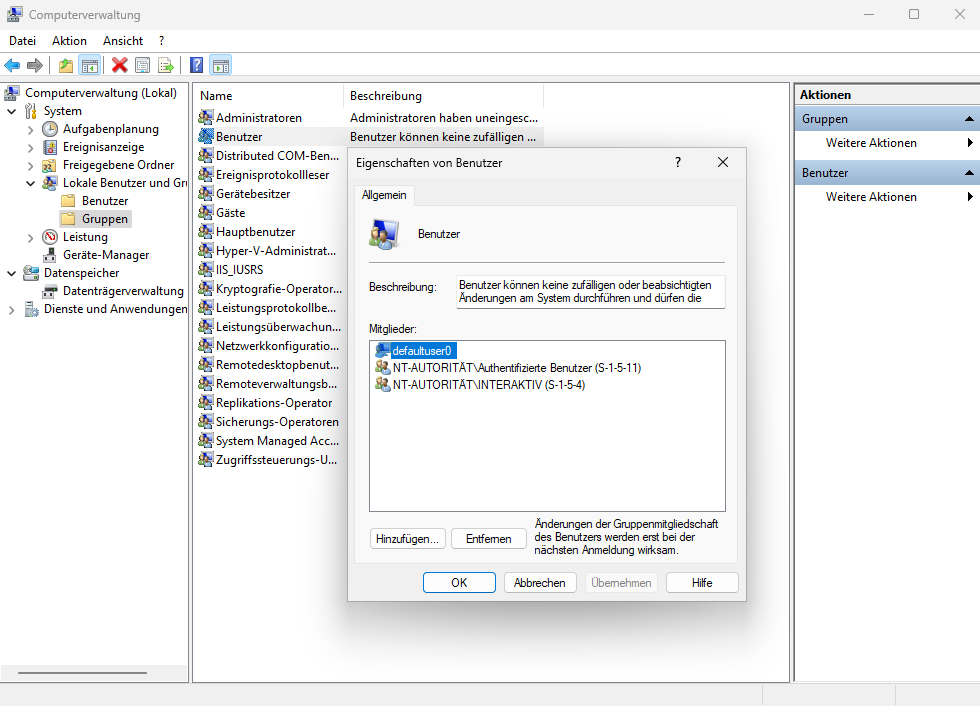
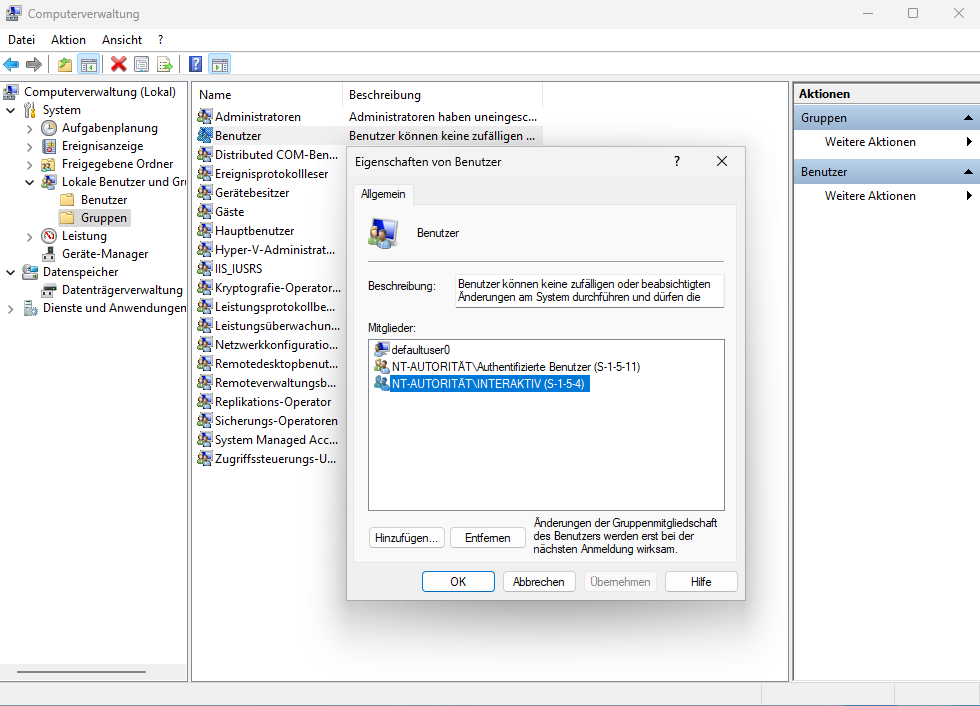
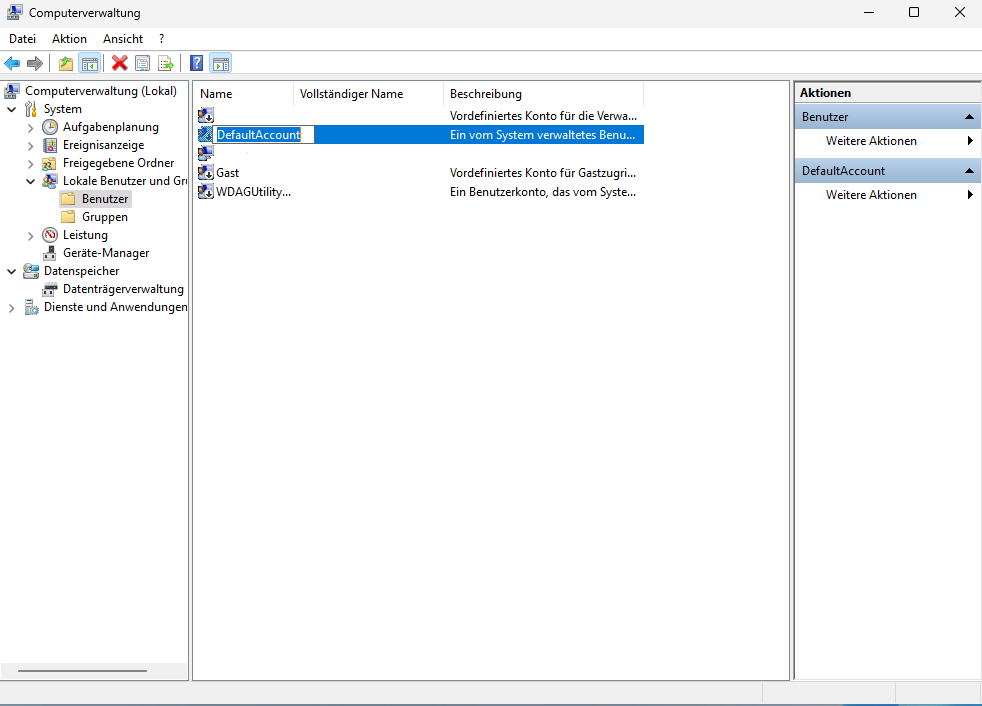
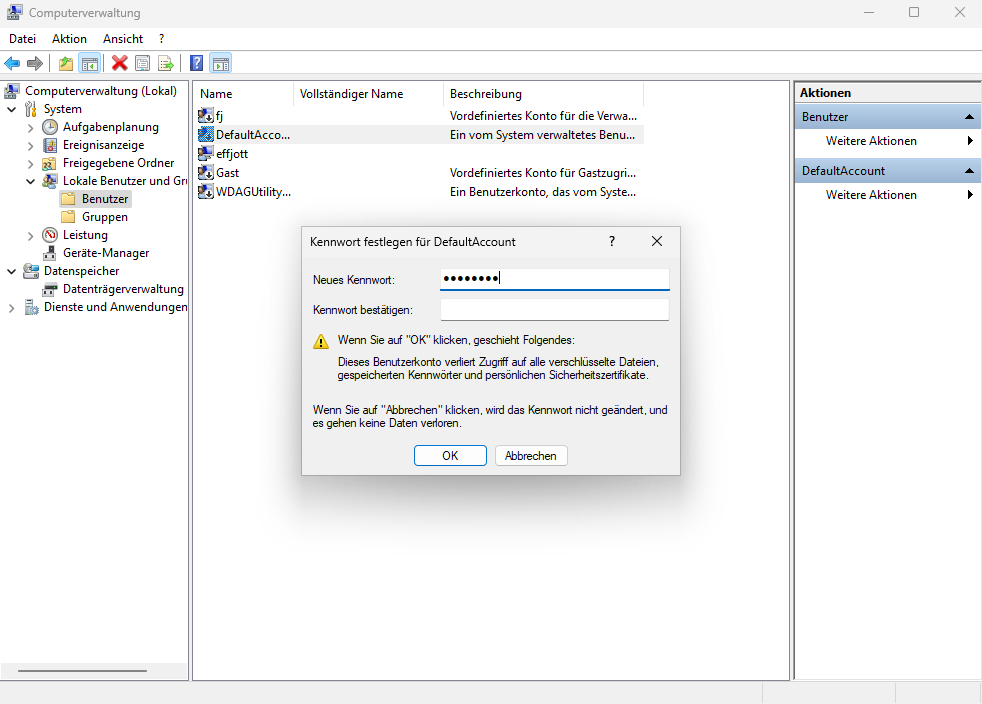

after an exciting week of trial and error and finding out which unknown person spoofed under my running operating system, reprogrammed my hard drive header and installed a virtual drive to infect my windows so that you don't notice it.
it was found:
3MB virtual boot lead to
8MB boot in MBR format may lead to
17MB and 230MB GPT boot+efi which lead to
1,8GB OS in form of about size revi.os and to a total of
2,8GB of unused harddisk space.
i was able to extract a registration file from this virtual OS (win) and save it in *.TXT format. i also disabled it as a precaution.
does anyone have a hot wire or expertise, an idea or good tricks?
at this point i am currently stuck except that i have been able to isolate everything so far to prevent and no longer allow this connection from my own computer to the other.
i put the file on my google drive since it is quite large (115MB) and cannot be uploaded here.
THE FILE IS A
*:TXT
contains all information about this #network under my windows version







