- Joined
- Oct 9, 2007
- Messages
- 47,774 (7.41/day)
- Location
- Dublin, Ireland
| System Name | RBMK-1000 |
|---|---|
| Processor | AMD Ryzen 7 5700G |
| Motherboard | Gigabyte B550 AORUS Elite V2 |
| Cooling | DeepCool Gammax L240 V2 |
| Memory | 2x 16GB DDR4-3200 |
| Video Card(s) | Galax RTX 4070 Ti EX |
| Storage | Samsung 990 1TB |
| Display(s) | BenQ 1440p 60 Hz 27-inch |
| Case | Corsair Carbide 100R |
| Audio Device(s) | ASUS SupremeFX S1220A |
| Power Supply | Cooler Master MWE Gold 650W |
| Mouse | ASUS ROG Strix Impact |
| Keyboard | Gamdias Hermes E2 |
| Software | Windows 11 Pro |
Dell notebooks and desktops dating all the way back since 2009—hundreds of millions of them the PC giant has shipped since—are vulnerable to unauthorized privilege escalation attacks, due to a faulty OEM driver the company uses to update the computer's BIOS or UEFI firmware, according to findings by cybersecurity researchers at SentinelLabs. "DBUtil," a driver that Dell machines load during automated or unattended BIOS/UEFI update processes initiated by the user from within the OS, is found to have vulnerabilities that malware can exploit to "escalate privileges from a non-administrator user to kernel mode privileges."
SentinelLabs chronicled its findings in CVE-2021-21551, which details five individual flaws. Two of these point out flaws that can escalate user privileges through controlled memory corruption, two with lack of input validation; and one with denial of service. Organizations that have remote updates enabled for their client machines are at risk, since the flaw can be exploited over network. "An attacker with access to an organization's network may also gain access to execute code on unpatched Dell systems and use this vulnerability to gain local elevation of privilege. Attackers can then leverage other techniques to pivot to the broader network, like lateral movement," writes SentielLabs in its paper.
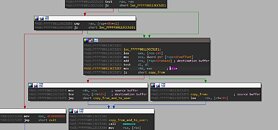
The good news here, is that SentinelLabs has been working with Dell before going public, and a patched DBUtil driver is ready. The company now stares at the daunting task of pushing patched drivers to potentially hundreds of millions of client PCs it shipped since 2009. The company put out a security advisory that describes CVE-2021-21551 to its end-users, and recommends the next course of action.
A video presentation by SentinelLabs follows.
View at TechPowerUp Main Site
SentinelLabs chronicled its findings in CVE-2021-21551, which details five individual flaws. Two of these point out flaws that can escalate user privileges through controlled memory corruption, two with lack of input validation; and one with denial of service. Organizations that have remote updates enabled for their client machines are at risk, since the flaw can be exploited over network. "An attacker with access to an organization's network may also gain access to execute code on unpatched Dell systems and use this vulnerability to gain local elevation of privilege. Attackers can then leverage other techniques to pivot to the broader network, like lateral movement," writes SentielLabs in its paper.

The good news here, is that SentinelLabs has been working with Dell before going public, and a patched DBUtil driver is ready. The company now stares at the daunting task of pushing patched drivers to potentially hundreds of millions of client PCs it shipped since 2009. The company put out a security advisory that describes CVE-2021-21551 to its end-users, and recommends the next course of action.
A video presentation by SentinelLabs follows.
View at TechPowerUp Main Site


 .
. .
.


