- Joined
- Oct 9, 2007
- Messages
- 47,783 (7.40/day)
- Location
- Dublin, Ireland
| System Name | RBMK-1000 |
|---|---|
| Processor | AMD Ryzen 7 5700G |
| Motherboard | Gigabyte B550 AORUS Elite V2 |
| Cooling | DeepCool Gammax L240 V2 |
| Memory | 2x 16GB DDR4-3200 |
| Video Card(s) | Galax RTX 4070 Ti EX |
| Storage | Samsung 990 1TB |
| Display(s) | BenQ 1440p 60 Hz 27-inch |
| Case | Corsair Carbide 100R |
| Audio Device(s) | ASUS SupremeFX S1220A |
| Power Supply | Cooler Master MWE Gold 650W |
| Mouse | ASUS ROG Strix Impact |
| Keyboard | Gamdias Hermes E2 |
| Software | Windows 11 Pro |
CTS-Labs, following up on Tuesday's "Masterkey" exploit proof-of-concept video, posted a guide to bypassing Windows Credential Guard on an AMD Ryzen-powered machine. We once again begin in a privileged shell session, of an AMD-powered machine whose Secure Processor that has been compromised using admin privileges, by exploiting it using any of the 13 vulnerabilities chronicled by CTS-Labs. Mimikatz, a tool that is used by hackers to steal network credentials, should normally not work on a machine with Windows Credential Guard enabled. Using a modified version of Mimikatz, the CTS-Labs researchers are able to bypass Windows Credential Guard (which relies on hardware-level security features present on the processor), leveraging the AMD Secure Processor malware microcode they wrote.
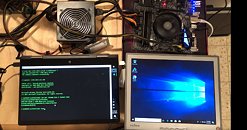
The proof-of-concept video follows.
View at TechPowerUp Main Site

The proof-of-concept video follows.
View at TechPowerUp Main Site






 at those saying there is no flaw, of course there's a flaw but it could have been dealt with 'properly' and had it been done so (been fixed by AMD), we would not have had all this hyperbolic forum activity.
at those saying there is no flaw, of course there's a flaw but it could have been dealt with 'properly' and had it been done so (been fixed by AMD), we would not have had all this hyperbolic forum activity.