Hello, I am French, forgive me for the poor writing of my post, it is probably not serious but the latest version of GPU-Z causes problems with Windows 11.
It's in French but experts will understand the Windows protection history screens.
It is not possible to install GPU-Z without removing the threat, I don't know why my Windows detects this and not others, otherwise there would be many messages here.
Simple reporting of the problem.
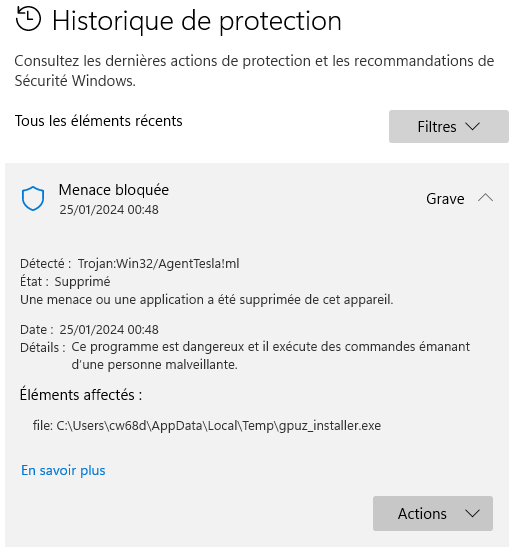
What it says in summary:
Serious threat blocked, malicious act/malware, removed and quarantined (another related alert indicates quarantine).
It's in French but experts will understand the Windows protection history screens.
It is not possible to install GPU-Z without removing the threat, I don't know why my Windows detects this and not others, otherwise there would be many messages here.
Simple reporting of the problem.
What it says in summary:
Serious threat blocked, malicious act/malware, removed and quarantined (another related alert indicates quarantine).






