- Joined
- Jun 24, 2015
- Messages
- 8,370 (2.28/day)
- Location
- Western Canada
| System Name | ab┃ob |
|---|---|
| Processor | 7800X3D┃5800X3D |
| Motherboard | B650E PG-ITX┃X570 Impact |
| Cooling | NH-U12A + T30┃AXP120-x67 |
| Memory | 64GB 6400CL32┃32GB 3600CL14 |
| Video Card(s) | RTX 4070 Ti Eagle┃RTX A2000 |
| Storage | 8TB of SSDs┃1TB SN550 |
| Case | Caselabs S3┃Lazer3D HT5 |
So my system lists a microcode update as of today. Seems like the focus of this one is on SA-00329 and SA-00320.
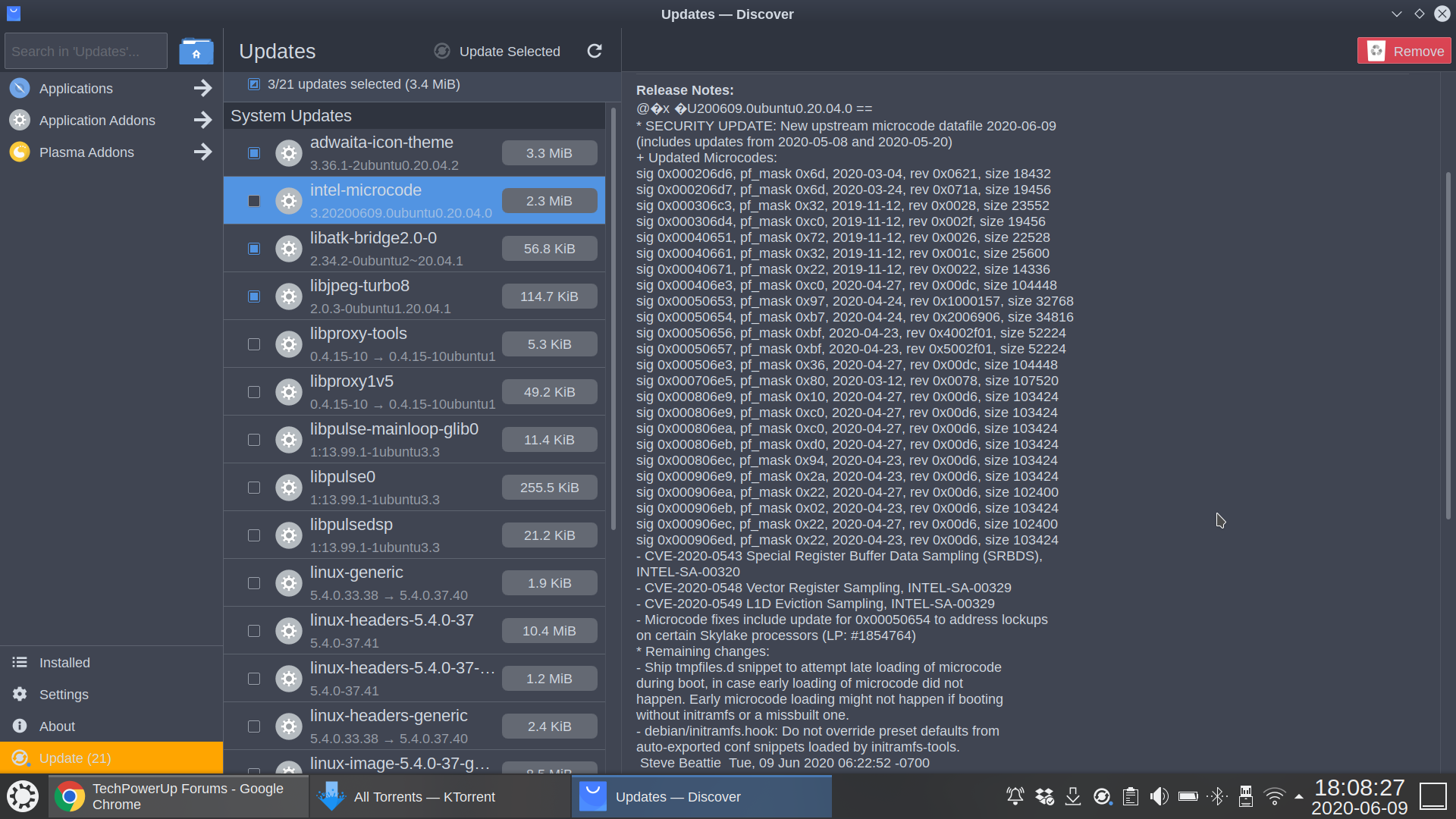
The former seems to patch the L1D exploit that's been floating around as of late, but the patch notes state that there is no known vulnerability using said exploit. I'm no expert on this, so all I know on the subject is that Linus Torvalds blasted Amazon's patch for L1D for being inappropriately heavy handed and performance-impacting in implementing mandatory flushing of L1D cache. Seems this patch does the same.
The latter SRBDS seems to be some sort of new strain of MDS surrounding RDRAND. I don't know anything about this, but others seem to:

Irony is that apparently SGX Enabled is a suitable protection for this vulnerability. I can't use SGX because I need undervolting on both Windows and Linux which means I can't use the Plundervolt (SA-00289) mitigation, in turn meaning it was safer to keep SGX off in that situation if not running the microcode update.
I don't usually care much for these in relation to my old 4790K, but this is my laptop with a 8550U and Hyperthreading already necessarily disabled for thermal throttling reasons, so if there's a bigger performance impact to these mitigations (which some of these technical reports seem to suggest) I wonder if it's better just to go without the microcode.
Thoughts on whether the microcode is worth it? The two vulnerabilities are rated at 2.8 and 6.5 out of 10, so not quite on the same level as the more famous exploits. The SRBDS vulnerability affects all Core from Ivy Bridge to Comet Lake-U, but apparently not Comet-H or Comet-S.
The former seems to patch the L1D exploit that's been floating around as of late, but the patch notes state that there is no known vulnerability using said exploit. I'm no expert on this, so all I know on the subject is that Linus Torvalds blasted Amazon's patch for L1D for being inappropriately heavy handed and performance-impacting in implementing mandatory flushing of L1D cache. Seems this patch does the same.
The latter SRBDS seems to be some sort of new strain of MDS surrounding RDRAND. I don't know anything about this, but others seem to:
Irony is that apparently SGX Enabled is a suitable protection for this vulnerability. I can't use SGX because I need undervolting on both Windows and Linux which means I can't use the Plundervolt (SA-00289) mitigation, in turn meaning it was safer to keep SGX off in that situation if not running the microcode update.
I don't usually care much for these in relation to my old 4790K, but this is my laptop with a 8550U and Hyperthreading already necessarily disabled for thermal throttling reasons, so if there's a bigger performance impact to these mitigations (which some of these technical reports seem to suggest) I wonder if it's better just to go without the microcode.
Thoughts on whether the microcode is worth it? The two vulnerabilities are rated at 2.8 and 6.5 out of 10, so not quite on the same level as the more famous exploits. The SRBDS vulnerability affects all Core from Ivy Bridge to Comet Lake-U, but apparently not Comet-H or Comet-S.
