Monday, August 5th 2019

NVIDIA Issues Warning to Upgrade Drivers Due to Security Patches
NVIDIA has found a total of five security vulnerabilities with its Windows drivers for GeForce, Quadro and Tesla lineup of graphics cards. These new security risks are labeled as very dangerous and have the potential to cause local code execution, denial of service, or escalation of privileges, unless the system is updated. Users are advised to update their Windows drivers as soon as possible in order to stay secure and avoid all of these vulnerabilities, so be sure to check your drivers for latest version. Exploits are only accessible on Windows based OSes, starting from Windows 7 to Windows 10.
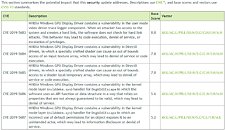
However, one fact that's reassuring is that in order to exploit a system, attacker must have local access to the machine that is running NVIDIA GPU, as remote exploit can not happen. Bellow are the tables provided by NVIDIA that show type of exploit along with rating it carries and which driver versions are affected. There are no mitigations for this exploit, as driver update is the only available solution to secure the system.The vulnerabilities are rated using CVSS V3 base scoring system and they are arranged as following:
However, one fact that's reassuring is that in order to exploit a system, attacker must have local access to the machine that is running NVIDIA GPU, as remote exploit can not happen. Bellow are the tables provided by NVIDIA that show type of exploit along with rating it carries and which driver versions are affected. There are no mitigations for this exploit, as driver update is the only available solution to secure the system.The vulnerabilities are rated using CVSS V3 base scoring system and they are arranged as following:
- CVE-2019-5683 - Most dangerous of all the vulnerabilities. This exploits uses driver's trace logger weakness to create hard links, that software does not check. Attacker could create any link without getting warned by the system and force local code execution, denial of service or escalation of privileges. It is rated with a score of 8.8.
- CVE-2019-5684 - Vulnerability which uses carefully crafted shaders in order to cause out of bounds access to input texture array, possibly leading to denial of service or code execution. It is rated with a score of 7.8
- CVE-2019-5685 - Vulnerability which also uses carefully crafted shaders in order to cause out of bounds access to shader local temporary array, possibly leading to denial of service or code execution as well. It is rated with a score of 7.8
- CVE-2019-5686 - Vulnerability hidden in kernel mode layer handler for DxgkDdiEscape, which uses different data structures and DirectX API functions that are not always valid, leading to denial of service if the API function or data structure is incorrect. It is rated with a score of 5.6.
- CVE-2019-5687 - Least dangerous exploit of all five. It is also a problem in kernel model layer handler for DxgkDdiEscape, which may put system at risk if incorrect default permissions are used for an object. This can lead to information disclosure or denial of service. It is rated with a score of 5.2.

32 Comments on NVIDIA Issues Warning to Upgrade Drivers Due to Security Patches
I would not be surprised if someday the nvidia telemetry components come back and bite them though... they most certainly talk to the net.
Touche. It's certainly doable for high value targets.