Raevenlord
News Editor
- Joined
- Aug 12, 2016
- Messages
- 3,755 (1.17/day)
- Location
- Portugal
| System Name | The Ryzening |
|---|---|
| Processor | AMD Ryzen 9 5900X |
| Motherboard | MSI X570 MAG TOMAHAWK |
| Cooling | Lian Li Galahad 360mm AIO |
| Memory | 32 GB G.Skill Trident Z F4-3733 (4x 8 GB) |
| Video Card(s) | Gigabyte RTX 3070 Ti |
| Storage | Boot: Transcend MTE220S 2TB, Kintson A2000 1TB, Seagate Firewolf Pro 14 TB |
| Display(s) | Acer Nitro VG270UP (1440p 144 Hz IPS) |
| Case | Lian Li O11DX Dynamic White |
| Audio Device(s) | iFi Audio Zen DAC |
| Power Supply | Seasonic Focus+ 750 W |
| Mouse | Cooler Master Masterkeys Lite L |
| Keyboard | Cooler Master Masterkeys Lite L |
| Software | Windows 10 x64 |
The Spectre/Meltdown road is long and pocked with lawsuits and security holes as it is, and Microsoft is one of the players that's trying to put the asphalt back to tip-top, Autobahn-worth shape. The company has already improved users' security to the Meltdown and Spectre exploits on its OS side; however, hardware patches, and specifically BIOS-editing ones are much harder to deploy and distribute by the PC chain. That may be one of the reasons why Microsoft is now again stepping up with software-based mitigations for Intel-based systems, specifically.
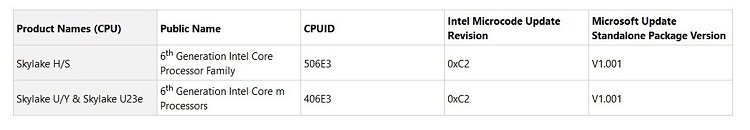
The new updates introduce a software-based CPU microcode revision update, and work at the OS-level to plug some security holes on your Intel processors that might otherwise remain unpatched. The reasons for them remaining unpatched can be many: either Intel taking even more time to deploy patches to the still vulnerable systems; your OEMs not deploying the Intel CPU microcode revisions via a BIOS update; or the good old "I forgot I could do it" user story. Of course, being software based means these Microsoft patches will have to be reapplied should users format their Windows system. The update can for now only be manually downloaded and installed, and can only be applied to version 1709 (Fall Creators Update) and Windows Server version 1709 (Server Core), but that's definitely better than the alternative of forcing less knowledgeable users to try and find their way through BIOS updates. Of course, that is assuming OEMs will ever push BIOS updates to their products.

View at TechPowerUp Main Site
The new updates introduce a software-based CPU microcode revision update, and work at the OS-level to plug some security holes on your Intel processors that might otherwise remain unpatched. The reasons for them remaining unpatched can be many: either Intel taking even more time to deploy patches to the still vulnerable systems; your OEMs not deploying the Intel CPU microcode revisions via a BIOS update; or the good old "I forgot I could do it" user story. Of course, being software based means these Microsoft patches will have to be reapplied should users format their Windows system. The update can for now only be manually downloaded and installed, and can only be applied to version 1709 (Fall Creators Update) and Windows Server version 1709 (Server Core), but that's definitely better than the alternative of forcing less knowledgeable users to try and find their way through BIOS updates. Of course, that is assuming OEMs will ever push BIOS updates to their products.


View at TechPowerUp Main Site

