AMD "Zen 1" to "Zen 4" Processors Affected by Microcode Signature Verification Vulnerability
Google Security Research team has just published its latest research on a fundamental flaw in the microcode patch verification system that affects AMD processors from "Zen 1" through "Zen 4" generations. The vulnerability stems from an inadequate hash function implementation in the CPU's signature validation process for microcode updates, enabling attackers with local administrator privileges (ring 0 from outside a VM) to inject malicious microcode patches, potentially compromising AMD SEV-SNP-protected confidential computing workloads and Dynamic Root of Trust Measurement systems. Google disclosed this high-severity issue to AMD on September 25, 2024, leading to AMD's release of an embargoed fix to customers on December 17, 2024, with public disclosure following on February 3, 2025; however, due to the complexity of supply chain dependencies and remediation requirements, comprehensive technical details are being withheld until March 5, 2025, allowing organizations time to implement necessary security measures and re-establish trust in their confidential compute environments.
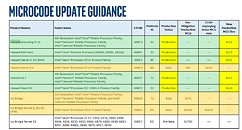
AMD has released comprehensive mitigation measures through AGESA firmware updates across its entire EPYC server processor lineup, from the first-generation Naples to the latest Genoa-X and Bergamo architectures. The security patch, designated as CVE-2024-56161 with a high severity rating of 7.2, introduces critical microcode updates: Naples B2 processors require uCode version 0x08001278, Rome B0 systems need 0x0830107D, while Milan and Milan-X variants mandate versions 0x0A0011DB and 0x0A001244 respectively. For the latest Genoa-based systems, including Genoa-X and Bergamo/Siena variants, the required microcode versions are 0x0A101154, 0x0A10124F, and 0x0AA00219. These updates implement robust protections across all SEV security features - including SEV, SEV-ES, and SEV-SNP - while introducing new restrictions on microcode hot-loading capabilities to prevent future exploitation attempts.
AMD has released comprehensive mitigation measures through AGESA firmware updates across its entire EPYC server processor lineup, from the first-generation Naples to the latest Genoa-X and Bergamo architectures. The security patch, designated as CVE-2024-56161 with a high severity rating of 7.2, introduces critical microcode updates: Naples B2 processors require uCode version 0x08001278, Rome B0 systems need 0x0830107D, while Milan and Milan-X variants mandate versions 0x0A0011DB and 0x0A001244 respectively. For the latest Genoa-based systems, including Genoa-X and Bergamo/Siena variants, the required microcode versions are 0x0A101154, 0x0A10124F, and 0x0AA00219. These updates implement robust protections across all SEV security features - including SEV, SEV-ES, and SEV-SNP - while introducing new restrictions on microcode hot-loading capabilities to prevent future exploitation attempts.