Tuesday, March 10th 2020

AMD Processors Since 2011 Hit with Cache Attack Vulnerabilities: Take A Way
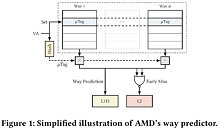
Cybersecurity researcher Moritz Lipp and his colleagues from the Graz University of Technology and the University of Rennes uncovered two new security vulnerabilities affecting all AMD CPU microarchitectures going back to 2011, detailed in a research paper titled "Take A Way." These include "Bulldozer" and its derivatives ("Piledriver," "Excavator," etc.,) and the newer "Zen," "Zen+," and "Zen 2" microarchitectures. The vulnerabilities are specific to AMD's proprietary L1D cache way predictor component. It is described in the security paper's abstract as a means for the processor to "predict in which cache way a certain address is located, so that consequently only that way is accessed, reducing the processor's power consumption."
By reverse engineering the L1D cache way predictor in AMD microarchitectures dating from 2011 to 2019, Lipp, et al, discovered two new attack vectors with which an attacker can monitor the victim's memory accesses. These vectors are named "Collide+Probe," and "Load+Reload." The paper describes the first vector as follows: "With Collide+Probe, an attacker can monitor a victim's memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core." The second vector is described as "With Load+Reload, we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core." The two vulnerabilities have not been assigned CVE entries at the time of this writing. The research paper, however, describes the L1D cache way predictor in AMD processors as being vulnerable to attacks that can reveal contents of memory or even keys to a vulnerable AES implementation. For now there is no mitigation to these attacks, but the company is reportedly working on firmware and driver updates. Access the research paper here.
Source:
Cowcotland
By reverse engineering the L1D cache way predictor in AMD microarchitectures dating from 2011 to 2019, Lipp, et al, discovered two new attack vectors with which an attacker can monitor the victim's memory accesses. These vectors are named "Collide+Probe," and "Load+Reload." The paper describes the first vector as follows: "With Collide+Probe, an attacker can monitor a victim's memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core." The second vector is described as "With Load+Reload, we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core." The two vulnerabilities have not been assigned CVE entries at the time of this writing. The research paper, however, describes the L1D cache way predictor in AMD processors as being vulnerable to attacks that can reveal contents of memory or even keys to a vulnerable AES implementation. For now there is no mitigation to these attacks, but the company is reportedly working on firmware and driver updates. Access the research paper here.
46 Comments on AMD Processors Since 2011 Hit with Cache Attack Vulnerabilities: Take A Way
I have a feeling that we will see more of this from now on, as the fruits of Intel's money become "published"...
I absolutely do not get the instant dismissal when someone spots Intel somewhere.Oh AMD... please never change?
In the referenced PDF, section 5.2.3, a method is described by which Javascript itself can be configured to attack a system and supply harvested data straight through both Chrome and Firefox browsers. Theoretically, ANY browser that uses Javascript(99%) can potentially be used to attack a subject system.
It will be interesting to review the analysis and CVE for these new vulnerabilities.
For the record, I don't dismiss the paper, it's not like I think it's nonsense but I do question it's purpose and how well it was timed with other events.
In line with the context used here, do you think we should dismiss any and all research papers Intel has been sponsoring? ;)What events? This was disclosed to AMD last August and published now. Timing a 6-month window would seem too big of a hassle to even try.
Edit:
This is kind of weird though. Instead of discussing what the paper found, whether this has impact or merit (it should, being an academic paper which I assume is peer reviewed), we are discussing Intel because there is a sidenote in the paper that Intel supported researchers. This kind of support is not exactly abnormal.
This research sponsoring is a legit method of competitive behaviour in my opinion and will lead to more secure products of all participants.
Much ado about nothing? Something?
If there is a vulnerability with AMD related products we condemn Intel once again..
There is never anything wrong with AMD.
The more pressure on the companies the greater the chance they do things right.
Same jokes as with Intel's vulns where the attacker already needs to have full admin access to the system?
Can this be used from outside sources without actual access?
Can this be exploited via malicious websites?
Those questions should be discussed here....
We can only hope these companies work better to maintain our security and not just to maintain market share.
To be fair researchers need pay too, and if intel were not paying some other nation state would be. probably would not disclose it to the company and would develop a zero day out of it, not good.
Finally hopefully And shore up this hole soon, somehow.