Wednesday, March 21st 2018

CTS-Labs Posts Ryzen Windows Credential Guard Bypass Proof-of-concept Video
CTS-Labs, following up on Tuesday's "Masterkey" exploit proof-of-concept video, posted a guide to bypassing Windows Credential Guard on an AMD Ryzen-powered machine. We once again begin in a privileged shell session, of an AMD-powered machine whose Secure Processor that has been compromised using admin privileges, by exploiting it using any of the 13 vulnerabilities chronicled by CTS-Labs. Mimikatz, a tool that is used by hackers to steal network credentials, should normally not work on a machine with Windows Credential Guard enabled. Using a modified version of Mimikatz, the CTS-Labs researchers are able to bypass Windows Credential Guard (which relies on hardware-level security features present on the processor), leveraging the AMD Secure Processor malware microcode they wrote.The proof-of-concept video follows.
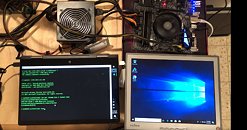
88 Comments on CTS-Labs Posts Ryzen Windows Credential Guard Bypass Proof-of-concept Video
They already dug up their hole , there ain't no getting out of it.
sudo rm -rf /*
and actually it is a joke...
Yes, we have tech news aggregation. Yes, we cover popular topics. Yes, we have opinions. But just because we cover a news story doesn't mean we hold to the opinion presented in the story. What it actually means is that we value your opinion, and want to hear what you think about the subject, presented in the light it is given. It's not financially motivated, either... we just care about what you think, and want to hear what you have to say. So please, say it, but please don't misinterpret our intent.
Any entity covering news/rumors/interviews and showing it to a public counts as journalism.
This was actually kind of refreshing - I learned quite a bit reading about these vulnerabilities.
www.techpowerup.com/242480/viceroy-research-and-cts-labs-make-their-positions-known-on-amd-flaws
I wonder if AMD might pursue a lawsuit for libel.
I also suspect ulterior motives myself given the nature of these CTS people and those connected to them. At best they seem to have found some vulnerabilities of questionable (in my opinion) severity (they're bad, but really hard to pull off) and are looking to profit from it. They're definitely not a legitimate security firm in my eyes, and their report is obviously made to benefit them, not to merely alert those concerned to the vulnerabilities.
That said, I've followed up on this for a while and read a lot of comments before immediately reaching for my e-torch and e-pitchfork... I don't dismiss the flaws as fake, rather overhyped because they would be very difficult to use in an actual attack against target systems. I also lump CTS in the came category as patent trolls and people who sue other people because their phone also has "rounded corners".
STH had a nice write-up on it from a legal perspective.
So honestly from what we know: They tried to act altruistic in their original disclosure all the while doing a hit and run on AMD. Their legal disclaimer directly contradicted that and they definitely received money for the job done in addition to leaking information to short sellers, possibly getting extra cash in that manner as well.
The security community agrees as well. Any future work by these guys is going to be tained by "well who's paying them this time?". I would not be surprised at all if this is the last public report this company does. They would be far better off creating a new company and trying to trick people that way.
Edit; just watched that video. This is, as demonstrated, not insignificant. This is serious and can be done quickly as the video shows.
This constant and pathetically lame referencing to "priviledged shell" or "admin authority" and whatnot is not the issue certain "people" are trying(and failing) to make it out to be. Finding systems on a network that have admin is not a difficult task, nor is artificially granting admin to a system that doesn't have it. If you don't understand these points, you have the problem.
People in such positions wouldn't be screaming the sky is falling either or running to replace the entire network when ever they get whim of a new exploit.
Lets weight this one out. Forum warriors screaming the sky is falling vs Security firm with 6yrs experience in the industry that got payed to review it with all the tools. Hmm.. tough call >Sarcasm<
That and the point there still is no valid update on CTS-Labs original "13 world-ending exploits" claim.
www.ctsflaws.com
Man these guys are probably looking to short CTS stock value. Oh wait, nvm
What's more disturbing is that they point to lax practices inside AMD and ASMedia in general. I don't like that. Not that that's anything unusual these days, but that's even more disturbing.
Seriously, if you are going to push "hardware security" try and give a shit about how the hardware thinks, please?