Microsoft's Windows 7 Reaches End-Of-Life
Today, on January the 14th, Microsoft is officially ending support for Windows 7 operating system. After more than 10 years since its launch, Windows 7 has remained a primary operating system on many PCs, especially OEM PCs manufactured before 2015, when Windows 10 came out. The user transition from Windows 7 to Windows 10 has not been an easy task for Microsoft, however, by declaring that the product has reached End-Of-Life, Microsoft is trying to make millions of users pull the trigger and embrace the new operating system.
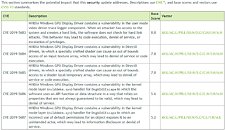
When January 14th arrives, Microsoft will stop giving Windows 7 users technical support, software updates with new features, and most importantly security updates. The official recommendation from Microsoft is to upgrade to the latest version of Windows, meaning Windows 10. As some of the older PCs may have compatibility issues with newer OS, it is also recommended to check your PC specifications. If you are a customer of the Extended Security Updates (ESU) program, you will continue to see further support in the future, however, for regular users, the support period is over.
When January 14th arrives, Microsoft will stop giving Windows 7 users technical support, software updates with new features, and most importantly security updates. The official recommendation from Microsoft is to upgrade to the latest version of Windows, meaning Windows 10. As some of the older PCs may have compatibility issues with newer OS, it is also recommended to check your PC specifications. If you are a customer of the Extended Security Updates (ESU) program, you will continue to see further support in the future, however, for regular users, the support period is over.